Mondorica
Toata lumea are un blog, de ce nu si eu ? Poate o sa fie si ceva interesant ... To be continue ...
sâmbătă, 23 martie 2024
Adapt the strace command to trace all processes belonging to a specific user
To adapt the strace command to trace all processes belonging to a specific user, you can use the -u option to specify the user. However, strace itself doesn't directly support tracing all processes of a user at once. You'll need to combine ps or pgrep with a loop to achieve this. Here's how you can do it:
#!/bin/bash
get_user_pids() {
pgrep -u "$1"
}
start_strace() {
strace -Z -p "$1" &
}
# Main loop
user="username"
while true; do
pids=$(get_user_pids "$user")
if [ -z "$pids" ]; then
echo "No processes found for user: $user"
sleep 10
continue
fi
for pid in $pids; do
if ! pgrep -f "strace.*-p $pid" > /dev/null; then
echo "Tracing PID: $pid"
start_strace "$pid"
fi
done
sleep 10
done
-Z Print only syscalls that returned with an error code.
Use man strace to adapt for your needs.
Save this script in a file, for example, monitor_username_activity.sh, and make it executable using the command chmod +x monitor_username_activity.sh.
sudo ./monitor_username_activity.sh
Replace "username" with the actual username of the user whose processes you want to trace. This script will find all processes belonging to that user and trace them using strace.
Make sure to run this script with appropriate permissions, as strace might require elevated privileges to trace some processes. Also, keep in mind that tracing all processes of a user can generate a significant amount of output and may impact system performance.
luni, 2 mai 2022
CAN YOU MAKE A WSL (UBUNTU) FILE SYSTEM VISIBLE FROM WINDOWS FILE EXPLORER?
Yes, in powershell, do (for example)
..user > subst W: '\\wsl$\Ubuntu-20.04\home\username\'
And you're in business. But, yes, I know what you're thinking - you don't want to do this manually.
You want to fire up WSL TTY (mintty) and have this DONE for you!
In your Ubuntu filesystem, maintain a file ending in a .ps1 extension and containing :
subst W: '\\wsl$\Ubuntu-20.04\home\analog\'
Then, in your .profile, just have :
powershell.exe -File /path/to/subst_cmd.ps1
(FYI, Thanks Thanh Phu, do delete this mapping, you'd do subst W: /D )
And you're through. Now, here's something trickier :
Without ever leaving WSL, how would you get Windows Firewall to allow communication between WSL
and the X-server you set up (follow Thomas Ward's excellent page to set up vcxsrv)
The answer :
Put this command in a file somewhere on windows (not Ubuntu) :
Set-NetFirewallProfile -DisabledInterfaceAliases "vEthernet (WSL)"
Then, all you do is :
powershell.exe -Command "Start-Process powershell.exe -ArgumentList \"-File C:\path\to\ps_fw_setting_WSL.ps1\" -Verb RunAs"
Which is something you could stick in your .profile
miercuri, 2 februarie 2022
Installing Linux - Ubuntu WSL - Apache Openmeeting Cluster - MSSQL as db
server-1:100.112.2.56
server-2:100.112.2.57
Network:100.112.2.0/24
In this setup is used MSSQL Cluster as db, if u will want to use another type of db should be sync,replicated ...
For this setup, location for records/stream/audio of openmeeting should be same for both servers, later u will see path /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT/webapps/openmeetings/data/streams which is an windows path as ( in this setup ) C:\Linux\ubuntu\rootfs\opt\openmeetings\openmeetings-server\target\apache-openmeetings-7.0.0-SNAPSHOT\webapps\openmeetings\data\streams
Fallow indications of actions on server-1, server-2 and on
both server
On both servers.
Invoke-WebRequest -Uri https://aka.ms/wsl-ubuntu-1804
-OutFile ubuntu.appx –UseBasicParsing
Rename-Item .\ubuntu.appx .\ubuntu.zip
Re-open Windows PowerShell ISE as Administrator
$userenv
=[System.Environment]::GetEnvironmentVariable("Path","User")
Open CMD as administrator
Enter the new user for your system
New CMD window, enter in location D:\Linux\ubuntu
Run command ubuntu1804.exe will enter you in the system with
root privilegies.
Reinstall openssh-server and create Schedule-Task, on both
server
On both servers.
visudo
%sudo ALL=NOPASSWD: /usr/sbin/sshd
service ssh --full-restart
Install prerequisites, on both server
#apt install imagemagick ghostscript libxt6 libxrender1 ffmpeg vlc sox openjdk-11-jdk openjdk-11-jdk-headless libjpeg62 zlib1g-dev openssl maven#vim /etc/ImageMagick-6/policy.xml...and comment the two follow lines, near to bottom file:
<policy domain="coder" rights="none"
pattern="PS" />
<policy domain="coder" rights="none"
pattern="PDF" />
...to:
<!-- <policy domain="coder"
rights="none" pattern="PS" /> -->
<!-- <policy domain="coder"
rights="none" pattern="PDF" /> -->
Fallow install steps of kurento media server – on both
servers.
https://doc-kurento.readthedocs.io/en/stable/user/installation.html#local-installation
#vim /etc/default/kurento-media-serverreplace
DAEMON_USER="kurento"
...to
DAEMON_USER="nobody"
After Kurento Media Server – install coturn STUN/TUN server
if behind a NAT
https://doc-kurento.readthedocs.io/en/stable/user/faq.html#faq-coturn-install
or
Install Coturn (Turn server), on both server:
#apt install coturn...we edit the following file so that the Turn server can
work:
# vim /etc/default/coturn...and we uncomment the line:
#TURNSERVER_ENABLED=1
….leaving it like this:
TURNSERVER_ENABLED=1
Now we'll set up Turn. Created a folder where turn server
store the logs:
#mkdir -p /var/log/turnserver...create a password that we'll need to put it in the configuration
file of the turn server and later in an
OpnMeetings file. We created it:
#openssl rand -hex 32...will generate something similar to this:
751c45cae60a2839711a94c8d6bf0089e78b2149ca602fdXXXXXXXXXXXXXXXXX
…copy that long password and paste it into a text file by
saving it.
Edit the turn configuration file:
#vim /etc/turnserver.conf...in this file we will have to uncomment (delete #) only
the following lines:
use-auth-secret
static-auth-secret=751c45cae60a2839711a94c8d6bf0089e78b2149ca602fdXXXXXXXXXXXXX
(on the above line put the long password we just saved in a
text file)
realm=your_real_domain ...change company.org to your real
domain
stale-nonce=0 ...change 600 to 0 (zero)
log-file=/var/log/turnserver/turnserver.log .
(above change /var/log/turnserver.log to
/var/log/turnserver/turnserver.log)
Install LibreOffice 7.2.3.2 – both servers
#add-apt-repository ppa:libreoffice/ppa#apt update#apt install libreofficeInstall MariaDB 10.1 ( if no other
database engine ) – excluded from this setup. Is MSSQL used.
( No install, on both servers )
#apt install install mariadb-server#mysql_secure_installationCreate database and user for
openmeeting
#mysqladmin -u root password colanda1MariaDB [(none)]> CREATE DATABASE open620 DEFAULT CHARACTER SET 'utf8';MariaDB [(none)]> GRANT ALL PRIVILEGES ON open620.* TO 'openmeeting'@'localhost' IDENTIFIED BY '1a2B3c4D' WITH GRANT OPTION;MariaDB [(none)]> FLUSH PRIVILEGES;* open620 ......is the database
name.
* openmeeting ………is the user name
for this database.
* 1a2B3c4D ..is the password for
this user.
Install Openmeeting 6.2.0 ( 7.0.0 released 3 ) – on both servers.
#cd /opt...get and build from source the OpenMeetings:
...build it:
...untar archive:
#cd /opt/openmeetings/openmeetings-server/target/#tar -zxvf apache-openmeetings-7.0.0-SNAPSHOT.tar.gz We make some folders for the recordings we´ll make at the
different OpenMeetings rooms:
#mkdir -p /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT/webapps/openmeetings/data/streams/{1,2,3,4,5,6,7,8,9,10,11,12,13,14}#mkdir -p /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT/webapps/openmeetings/data/streams/hibernate...restrict the access to these folders:
#chmod -R 750 /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT/webapps/openmeetings/data/streams...and we do to “nobody” user ownner of OpenMeetings
installation folder:
#chown -R nobody:nogroup /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOTDownload and install the connector between OpenMeetings and
MariaDB ( if no other database engine ):
#cd /opt#wget https://repo1.maven.org/maven2/mysql/mysql-connector-java/8.0.27/mysql-connector-java-8.0.27.jar...and copy it to where must be:
#cp /opt/mysql-connector-java-8.0.27.jar /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT/webapps/openmeetings/WEB-INF/libScript to launch Tomcat-OpenMeetings – on both servers.
Create file /etc/init.d/tomcat4
with …
#!/bin/sh # set the environment# JAVA_OPTS="-Djava.awt.headless=true -Djava.security.egd=file:/dev/./urandom"# CATALINA_OPTS=""export JAVA_OPTS="-Djava.awt.headless=true"CATALINA_HOME=/opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT #set TIMEOUT values#TIMELIMIT=10#SLEEPTIME=40 # Function to wait until all Tomcat processes are killedwaitForTomcatToDie(){ PROCESSES=`ps auxwww | grep $HOME | grep 'java' | grep 'tomcat' | grep -v 'grep'` while [ ! -z "${PROCESSES}" ] && [ ${SECONDS} -lt ${TIMELIMIT} ] && [ ${TIMELIMIT} -ne 0 ]; do echo -n "." sleep ${SLEEPTIME} PROCESSES=`ps auxwww | grep $USER | grep 'java' | grep 'tomcat' | grep -v 'grep'` done echo "" if [ ! -z "${PROCESSES}" ]; then PROCESS_ID=`echo ${PROCESSES} | awk '{ print $2 }'` echo "Killing process: ${PROCESS_ID}" kill -9 ${PROCESS_ID} fi} # See how we were called.case "$1" instart) #$CATALINA_HOME/bin/startup.sh cd ${CATALINA_HOME} sudo --preserve-env=CATALINA_HOME --preserve-env=JAVA_OPTS -u nobody ${CATALINA_HOME}/bin/startup.sh ;;#debug) #DEBUG_PORT=10001 #;;stop) cd ${CATALINA_HOME} sudo --preserve-env=CATALINA_HOME -u nobody ${CATALINA_HOME}/bin/shutdown.sh waitForTomcatToDie echo "...Tomcat stopped." ;;restart) $0 stop echo "...Restarting..." sleep 8 $0 start ;;status) status ${PROG} -p ${PIDFILE} RETVAL=$? ;;*) echo "Usage: $0 {start|stop|restart|status}" RETVAL=1esac exit ${RETVAL} ...and concede permission of execution:
#chmod +x /etc/init.d/tomcat4Run Tomcat-OpenMeetings
Start MariaDB, if still it is not (
if no other database engine ): ( No need in this setup )
# /etc/init.d/mysql start...and now start tomcat-OpenMeetings, only server-1:
Openmeeting link: https://localhost:5443/openmeetings
Configuration with MSSQL – server-1 ( only one server –first
node )
Configure Cluster node between server-1 and server-2
On server-1 and server-2 stop service of opemeeting.
#/etc/init.d/tomcat4 stop
Application might not stop and check
Take pid id and kill it
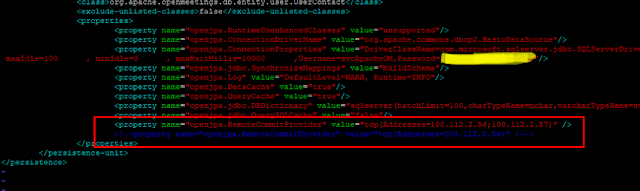
Configure persistence.xml server-1
#vim /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT/webapps/openmeetings/WEB-INF/classes/META-INF/persistence.xml
Add
<property name="openjpa.RemoteCommitProvider"
value="tcp(Addresses=100.112.2.56;100.112.2.57)" />
Comment
<!--property
name="openjpa.RemoteCommitProvider"
value="tcp(Addresses=100.112.2.56)" /-->
Configure hazelcast.xml
server-1:
#vim /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT/webapps/openmeetings/WEB-INF/classes/hazelcast.xmlAdd cluster name
<cluster-name>production</cluster-name>
Instance name must be unique
<instance-name>server-1</instance-name>
Attribute name must be same as Instance name
<attribute
name="name">server-1</attribute>
Server URL
<attribute name="server.url">https://100.112.2.56:5443/openmeetings</attribute>
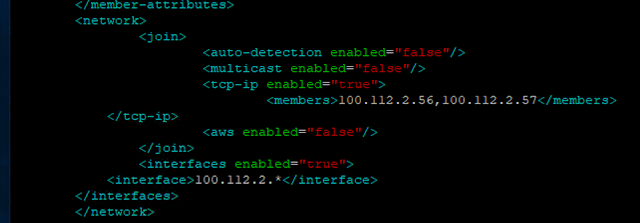
And network tag should be this
<network>
<join>
<auto-detection enabled="false"/>
<multicast enabled="false"/>
<tcp-ip enabled="true">
<members>100.112.2.56,100.112.2.57</members>
</tcp-ip>
<aws enabled="false"/>
</join>
<interfaces enabled="true">
<interface>100.112.2.*</interface>
</interfaces>
</network>
hazelcast.discovery.enabled
must be commented like in this image
<!--property name="hazelcast.discovery.enabled">false</property-->
Configure hazelcast.xml
server-2:
#vim /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT/webapps/openmeetings/WEB-INF/classes/hazelcast.xmlAdd cluster name
<cluster-name>production</cluster-name>
Instance name must be unique
<instance-name>server-2</instance-name>
Attribute name must be same as Instance name
<attribute name="name">server-2</attribute>
Server URL
<attribute name="server.url">https://100.112.2.57:5443/openmeetings</attribute>
And network tag should be this
<network>
<join>
<auto-detection enabled="false"/>
<multicast enabled="false"/>
<tcp-ip enabled="true">
<members>100.112.2.56,100.112.2.57</members>
</tcp-ip>
<aws enabled="false"/>
</join>
<interfaces
enabled="true">
<interface>100.112.2.*</interface>
</interfaces>
</network>
hazelcast.discovery.enabled
must be commented like in this image
<!--property
name="hazelcast.discovery.enabled">false</property-->
Configure persistence.xml server-2
Copy from server-1 /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT/webapps/openmeetings/WEB-INF/classes/META-INF/persistence.xml
Back-ul old file and replace with the content from server-1 file.
#cp /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT/webapps/openmeetings/WEB-INF/classes/META-INF/persistence.xml /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT/webapps/openmeetings/WEB-INF/classes/META-INF/persistence.xml.old
#vim /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT/webapps/openmeetings/WEB-INF/classes/META-INF/persistence.xml
Add content from server-1 file of persistence.xml to look
same.
...and now start tomcat-OpenMeetings, on both servers:
IF coturn got installed, openmeeting behind NAT
Edit the openmeetings.properties file of OpenMeetings – on
both servers:
#vim /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOT/ /webapps/openmeetings/WEB-INF/classes/openmeetings.properties...and in the ### Kurento ### section we modify only the
following lines:
#### Kurento ###
kurento.turn.url=
kurento.turn.user=
kurento.turn.secret=
...to
kurento.turn.url=Public IP of your server:3478
kurento.turn.user=
kurento.turn.secret=751c45cae60a2839711a94c8d6bf0089e78b2149ca602fdXXXXXXXXXXXXX
...above, in:
kurento.turn.secret=751c45cae60a2839711a94c8d6bf0089e78b2149ca602fdXXXXXXXXXXXXX
...replace the line:
751c45cae60a2839711a94c8d6bf0089e78b2149ca602fdXXXXXXXXXXXXX
...by the long password that we generated at coturn
installation and that we save in a text file
Now will make nobody owner of the OpenMeetings installation
directory, on both servers:
#chown -R nobody:nogroup /opt/openmeetings/openmeetings-server/target/apache-openmeetings-7.0.0-SNAPSHOTRestart coturn:
#/etc/init.d/coturn restartKurento:
#/etc/init.d/kurento-media-server restartTomcat-OpenMeetings:
#/etc/init.d/tomcat4 restartOpen ports required
3478 TCP-UDP IN
5443 TCP IN
8888 TCP IN
49152:65535 UDP IN-OUT
5701 TCP IN
5080 TCP IN
22 TCP IN
Checking cluster status:
Log in on both servers links, server-1 and server-2
Link server-1: https://100.112.2.56:5443/openmeetings/signin
Link server-2: https://100.112.2.57:5443/openmeetings/signin
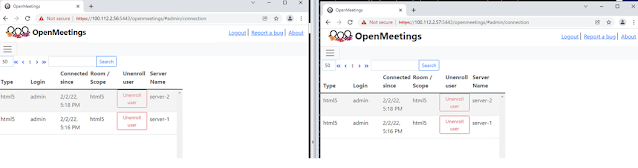
You can now login really to node1 and node2 of your cluster
while those users are loggedin and go to Administration
> Connections and check in the column "Server
Name" where they are located. They should be on different server.
The End